

Threat actors haven’t just become faster, they’ve become harder to find.
The old signals are fading. The broken grammar, the noisy login spikes, the simple fingerprints that once gave them away are gone. In their place is something quieter, more adaptive, and increasingly difficult to distinguish from normal behavior.
AI didn’t just change how attackers build their tools, it changed how they think. AI is not only the accelerator but the medium through which threat actors carry out sophisticated attacks themselves.
Vibe hacking means that threat actors no longer need to be highly technical to conduct attacks. The skills chasm between elite hackers and script kiddies has shortened to a blurred line. Now, the generative AI problem for defenders has shifted from volume to veracity. Payloads rewrite themselves between deliveries, and weaponized agents shift tactics mid-execution to achieve their objectives.
This shift demands a new kind of defense, one rooted in curiosity and human ingenuity, not reaction. An approach that augments any network defender into an elite threat hunter, and empowers hunters to use their ingenuity and creativity to stay one step ahead of the adversary: Vibe Hunting. Today, we’re excited to announce its general availability to all Nebulock customers.
What Is Vibe Hunting?
Vibe Hunting is the meeting of human intuition with machine reasoning. Agents built by hunters to democratize threat hunting. Not just another co-pilot or AI overlay, but an enabler for security teams to add threat hunting to their skillset whether there’s dedicated threat hunters or not.
Threat hunting has long been an esoteric, highly skilled mystery. Ask ten security teams to define it and you’ll get a dozen answers. For some, it’s a dedicated function. For others, it’s an instinctive process, a way to follow a hunch through the noise and see if it means something. Regardless of approach, cost remains the common denominator. Hunting takes time, skill, and context; three things network defenders rarely have in abundance.
We built Vibe Hunting to change that. Instead of memorizing syntax or switching between tools, defenders can start with their instincts and let the system do the translation.
Intuition is often the first signal that something is wrong. The small pattern you notice in a log line. The session that looks almost normal but doesn’t feel right. Those are the sparks that lead to discoveries, yet they’re often the first things lost in the thrash of day to day firefighting.
Vibe Hunting gives your curiosity a workflow.
When you describe an observation or a suspicion, Nebulock turns that intent into action. Our agentic hunters will guide you through the noise to find signal.
- Pre-prepared data and analysis: you don’t need to do the research, Nebulock distills intelligence and business context so you can hunt out of the box.
- Prompt-based hypothesis building: You describe behavior in natural language and follow through a full threat hunting workflow.
- Feedback loops with synthetic data: You can simulate attack behavior and see whether your detections would catch it.
- Fused context: Instead of bouncing between tools and notes, all your reasoning, telemetry, and threat intelligence live together.
- Closing the loop: translate hunts into behavioral detections, test and deploy them in minutes.
The goal isn’t to replace experience, it’s to make your experience easier to action.
How It Works
Hunting is about connecting what you feel to what you can prove. The problem is that most tools get in the way of that connection. You start with an idea, write a few queries, run them across your data, transform the data and then try to decide whether what you’re seeing is interesting or just noise. It’s a slow loop, and every step introduces friction, taking weeks to months to complete.
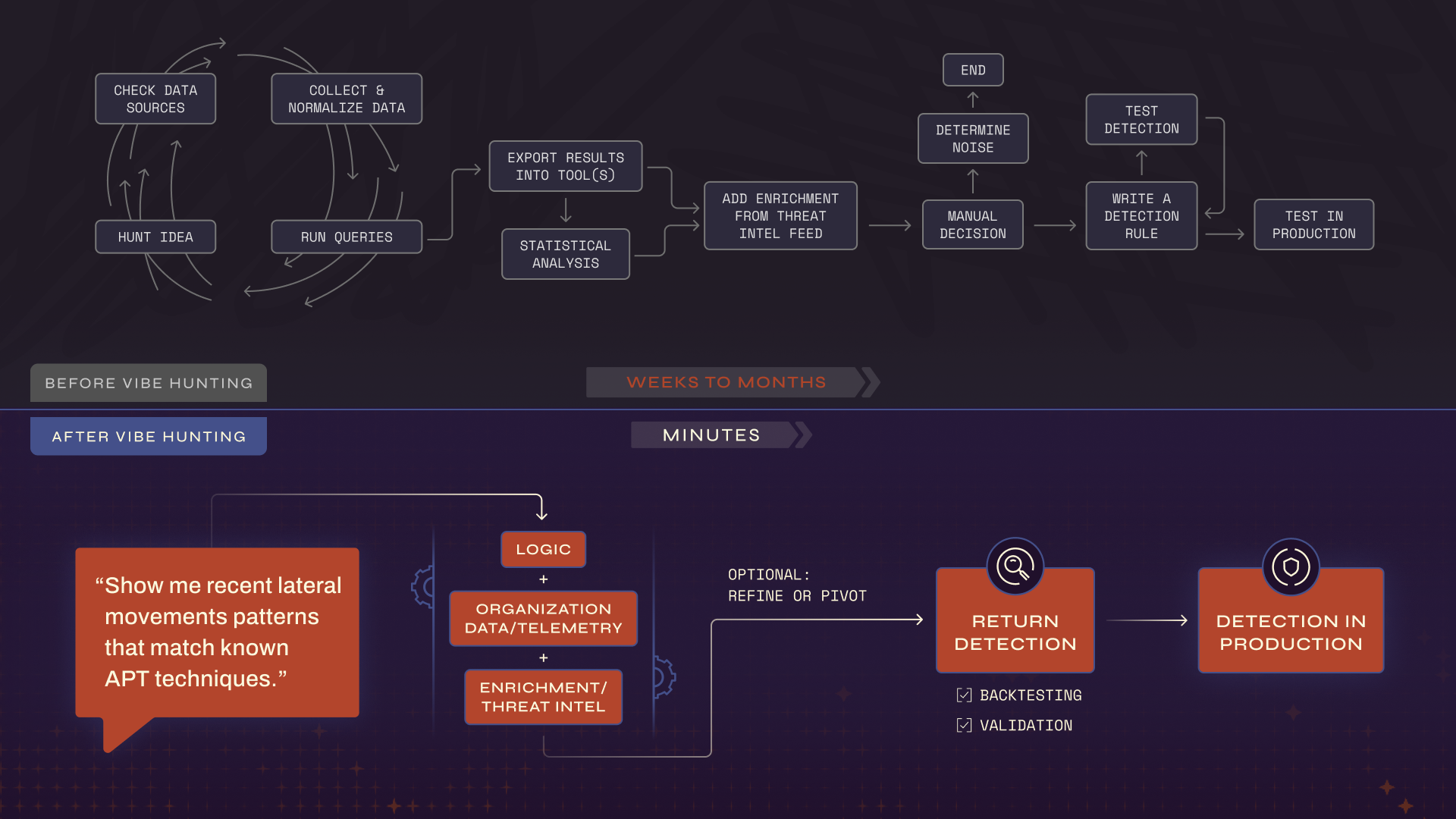
Vibe Hunting collapses that loop. You start with a question, something like “show me recent lateral movement patterns that match known APT techniques.” The system constructs the logic, runs it across your data, and returns the findings with context and confidence levels. You can immediately refine and pivot; exclude specific accounts, focus on certain endpoints, or pivot to persistence behaviors, and the model adapts, keeping track of your reasoning as it evolves. The result? A potential attack pathway identified in minutes rather than hours, with less cognitive load and more comprehensive results.
The hunt becomes a conversation. You’re still guiding it, still interpreting what you see, but without all the pauses that used to break your flow all while retaining context. Past hunts, previous detections, resolved incidents all of that context feeds back into the next question you ask. Each session builds on the one before it, so your hunts grow sharper over time.
This isn’t automation for automation’s sake. It’s a way to think faster, and to keep the thread between intuition and evidence intact.
Vibe Hunting Example
Let’s walk through a real-life scenario:
My CISO asks if we’ve been impacted by a new Scattered Spider TTP. No alerts, incidents, or anything reported.
Let’s vibe hunt this. I ask:
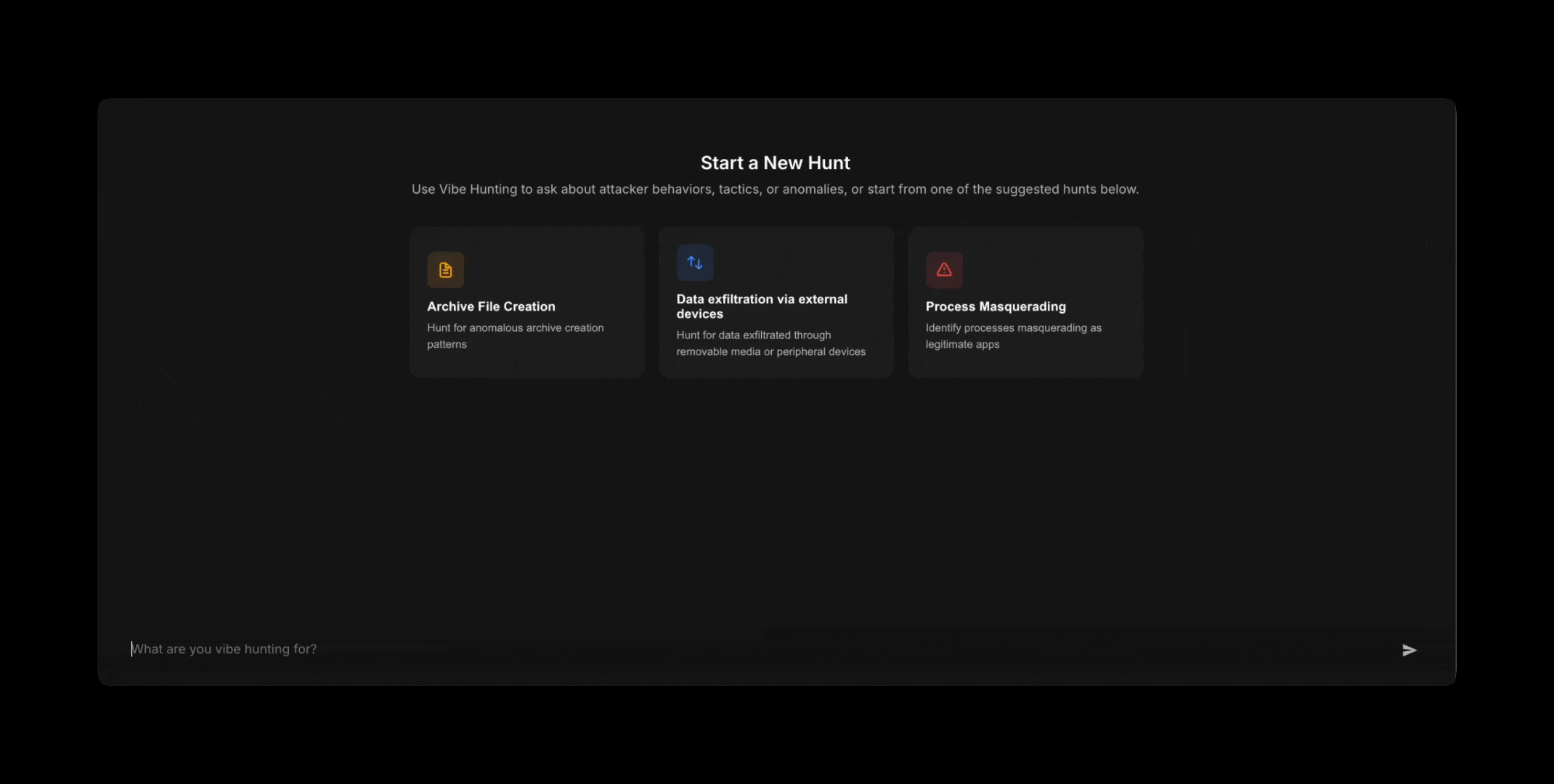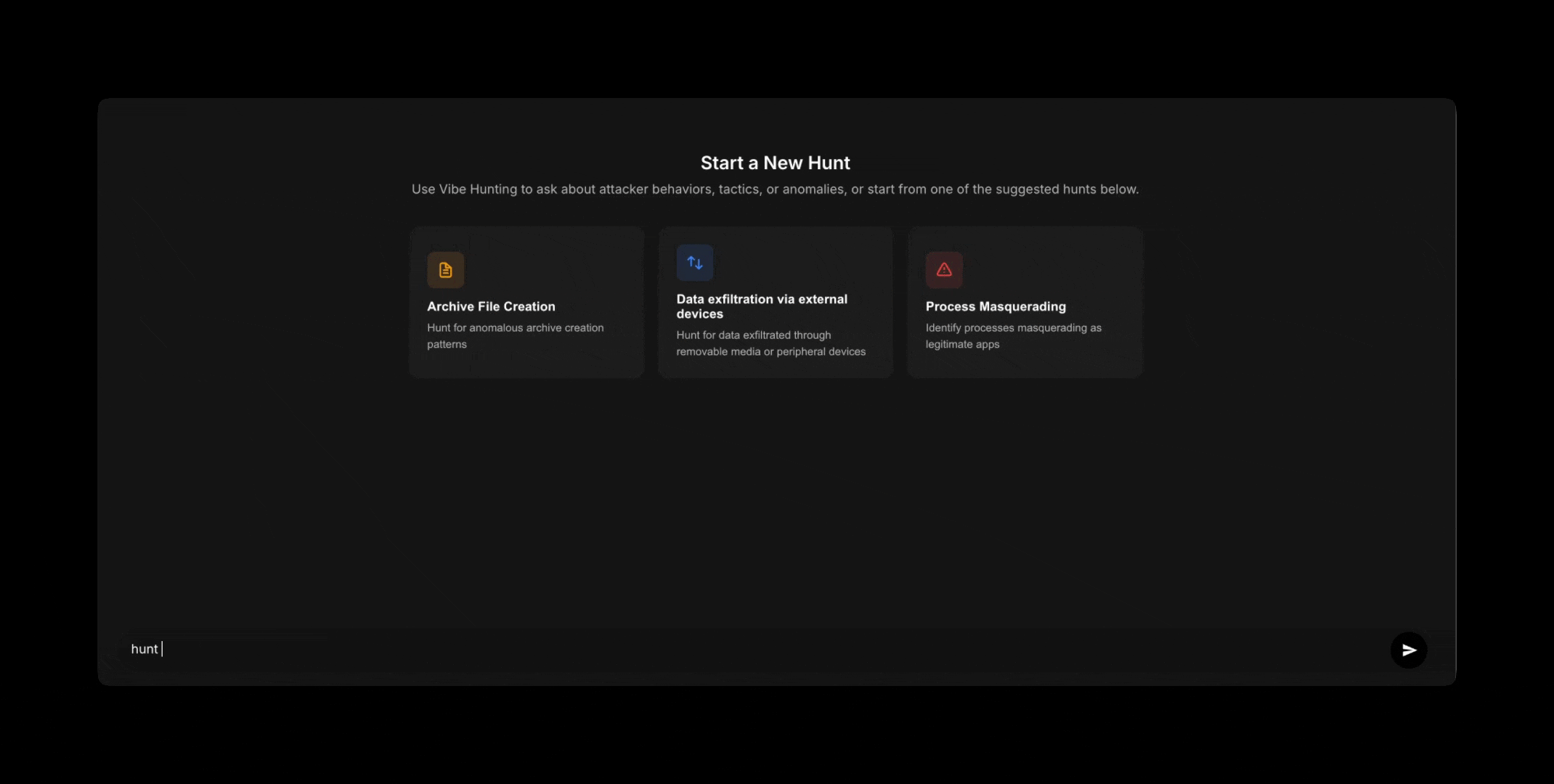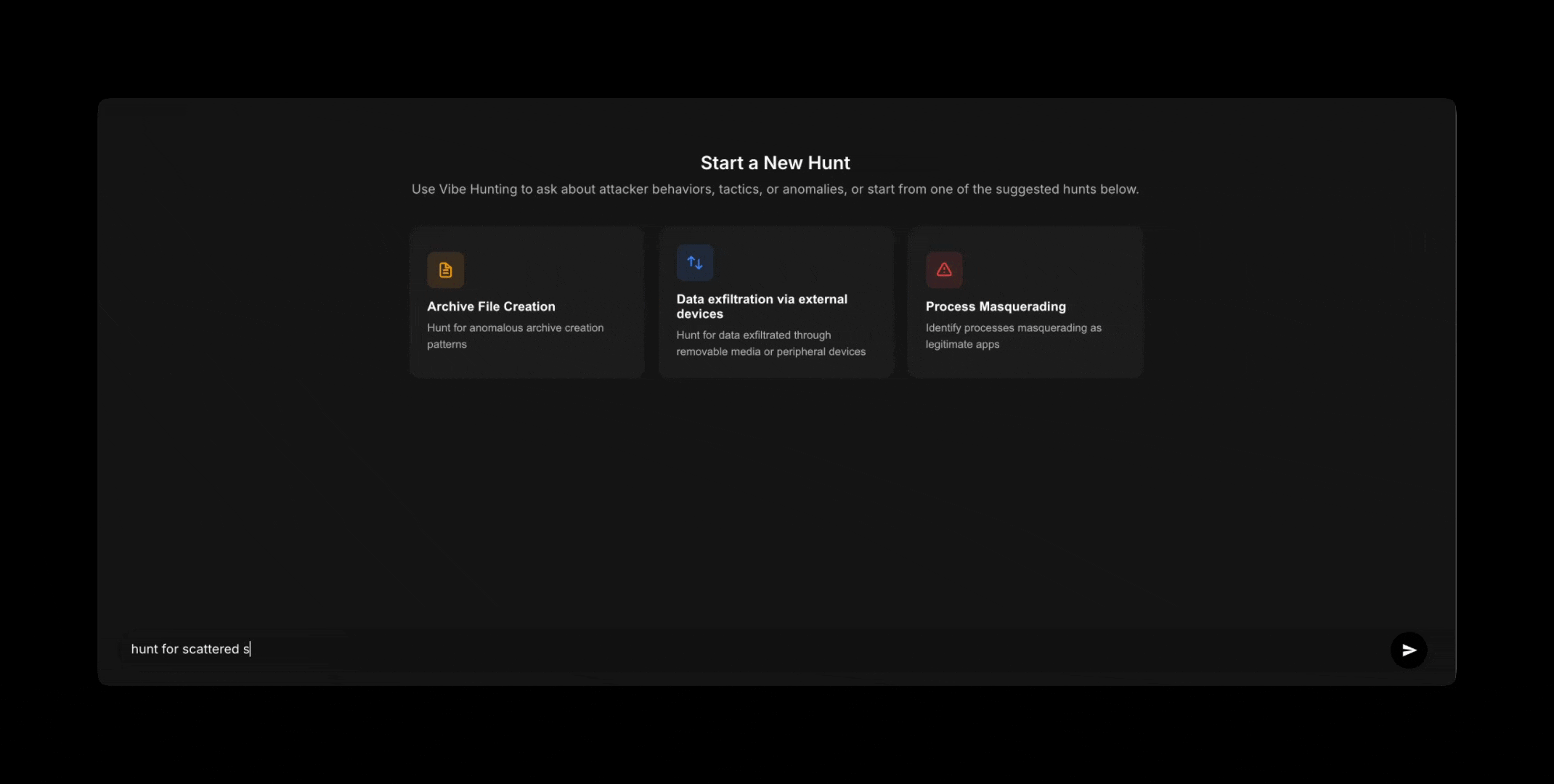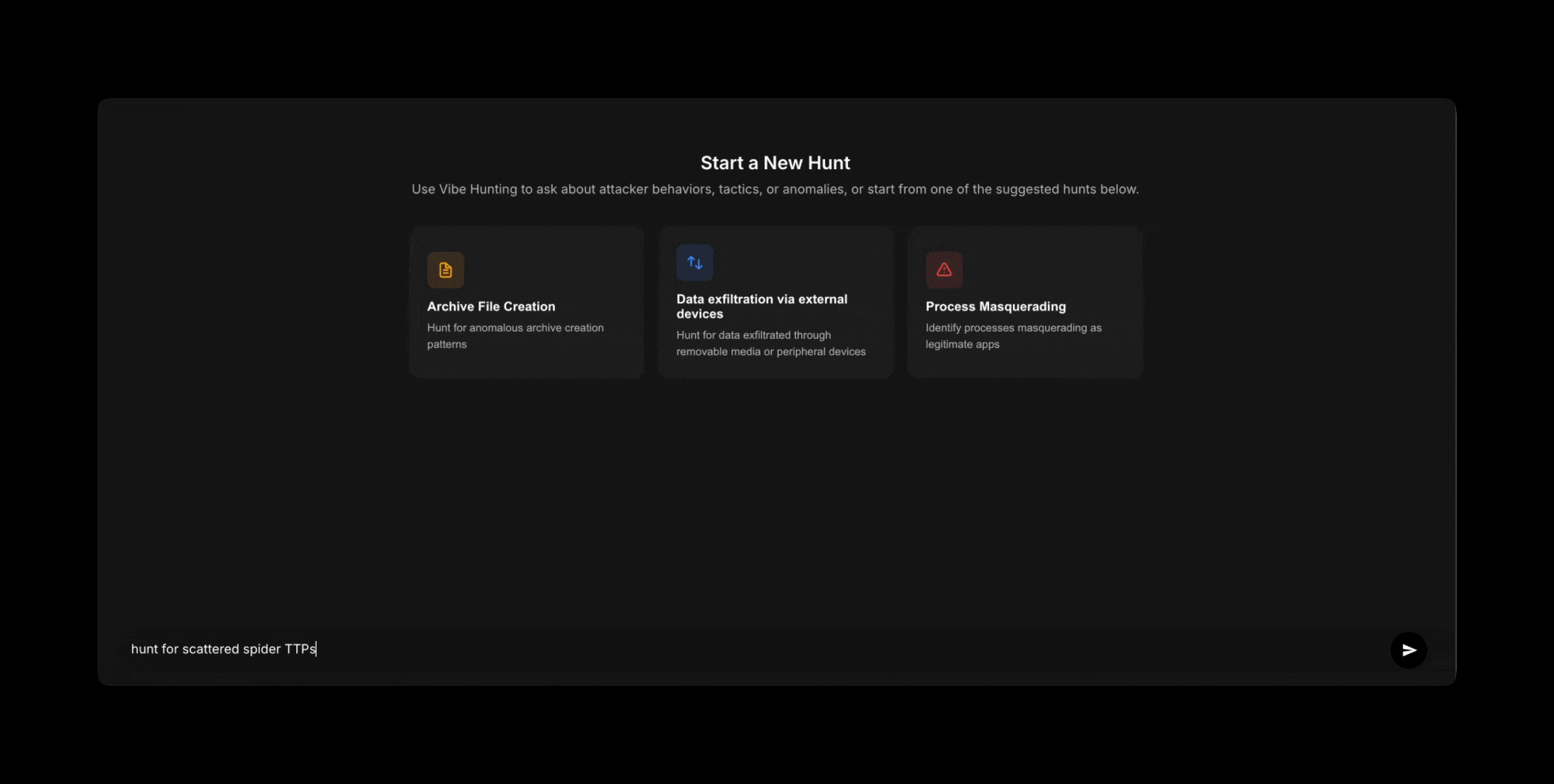
I know my data and telemetry is normalized to hunt on. The agent returns results and guides me further on my hunt:
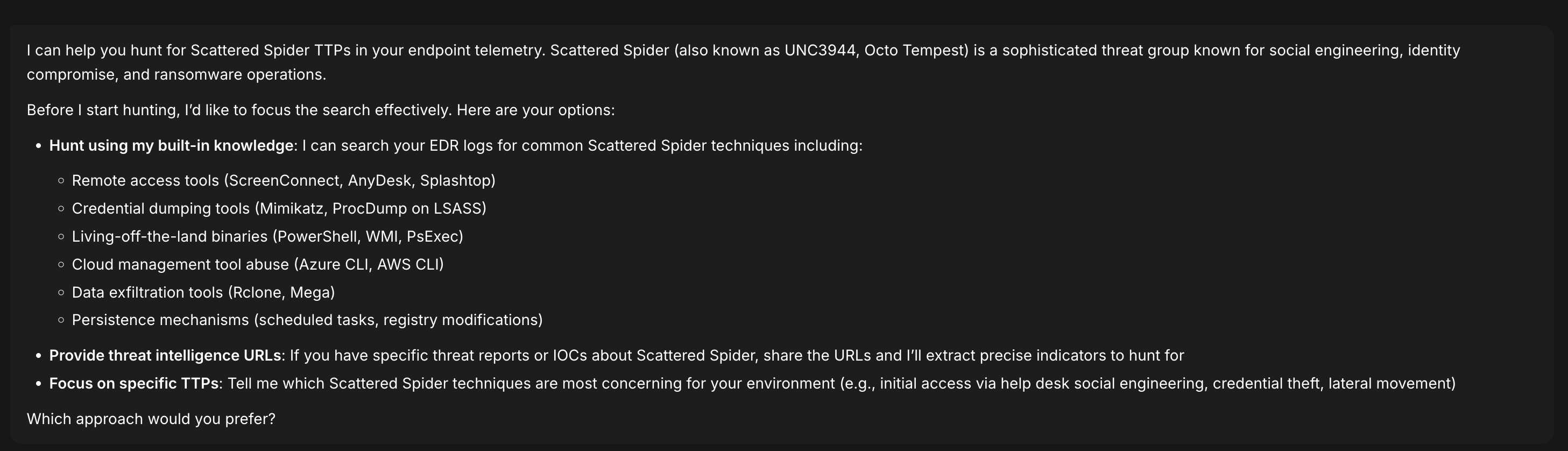
.png)
I’m not impacted, but I want a detective control.
.png)
Let me back test to determine validity.
.png)
Now I’m proactively covered.
.png)
Built by Hunters for Hunters
For most of us, hunting has always been a mix of instinct and patience, process is part science, part storytelling. Over time, though, it became more structured and less human. Tools multiplied, data grew, and the work shifted from exploring to sprint planning..
Vibe Hunting was born from a simple question: how can human creativity fuse with machine speed?
We imagined what it would look like if a network defender could have a running conversation with their environment, where the system listens, retrieves, and reasons in the background while the human focuses on patterns and decisions. If the hunt could feel less like writing code and more like asking questions that matter.
Once that happens, we hunt more often, we explore more. We unlock our creativity, following instincts that might otherwise go untested. Because when you remove friction, curiosity takes over, and that curiosity is where the best detections begin. But speed is only part of the story, what matters most is what happens after the hunt.
Each session should leave the organization stronger than before. If you confirm malicious behavior, Vibe Hunting helps you turn it into a reusable behavioral detection. If you uncover a blind spot, it becomes a visibility gap to prioritize. If the behavior is legitimate but risky, it becomes a control improvement or a policy change…even unfinished hunts add context for the next iteration. Each hunt strengthens the next. That is the feedback loop: intuition turning into evidence, and evidence into better defenses.
That is what Vibe Hunting was built for.
Where do we go from here?
Proactive defense isn’t a luxury anymore, it’s the baseline for the next phase of security, and vibe hunting makes that possible.
The 2026 PwC Global Digital Trust Insights Report found that threat hunting ranked as the top AI-related security priority for the next twelve months, above automation, orchestration, and even generative risk assessment. That signals a shift in mindset. Security leaders are realizing that curiosity, not just coverage, is what’s going to matter most.
Vibe Hunting is our way of helping defenders enable that curiosity at scale.
You can explore it now in the Vibe Hunting playground, or reach out if you want to see how it works in your environment.
The next generation of hunting starts here…and it begins, as always, with a good question.
Happy Hunting.
Subscribe Now
Get the latest Nebulock news direct to your inbox